I Built a Profitable Cybersecurity Education Program (Platform + Curriculum) From Scratch
- Zachary Jordan

- Sep 9, 2025
- 5 min read
Updated: Sep 10, 2025
Executive Summary
Problem: Security awareness that people actually finish, plus targeted whaling/BEC protection for executives—delivered on a startup budget.
Solution: I designed and launched a full education program and SaaS-style platform: content, app, analytics, identity/SSO, and ops.
Results (pilot snapshot):
Course completion 92% (up from ~40%).
Phishing click-through 22% → 6% in 90 days.
Time-to-report suspected phish 11h → 47m.
Executive drills adopted out-of-band payment verification org-wide.
Economics: ~$170/mo infra for ~1,000 learners; 85–93% gross margin at $15–$29/seat/year pricing.
Fit: Product + security hybrid who ships quickly, communicates with execs, and proves ROI with data.
1) Problem & Success Criteria
Traditional programs fail on two fronts:
Engagement. Hour-long videos and compliance slides do not change behavior.
Executive exposure. CEO and finance leaders are prime BEC targets; most programs don’t give them practical, repeatable drills.
Success metrics I committed to:
Completion rate ≥ 85% in 60 days
Phishing CTR reduced by 50% within 90 days
Median time-to-report (TTR) < 1 hour
Executives pass whaling drills with documented approval policy changes
Cost/learner low enough to maintain >80% gross margin
2) Constraints & Design Principles
Budget-first: commodity cloud, serverless where possible
Mobile-first micro-lessons: 5–7 minutes, single outcome per lesson
Measure everything: events → warehouse, cohort views
Privacy-by-design: collect the minimum, delete aggressively
Eight-week MVP: content + app + analytics + initial drills

Why this stack?
Next.js gives SEO + fast SSR; Tailwind keeps UI fast to iterate.
FastAPI/Node is lightweight; deployable on Lambda/Fargate.
Postgres for relational data; Redis for rate limits and queues.
CloudFront + S3 keeps media costs down and performance high.
PostHog + BigQuery means product-grade analytics without vendor lock-in.
4) Data & Security Model
PII minimization: store user email, role, department, and high-level event outcomes (e.g., “clicked simulation,” “reported phish”). No message bodies.
Encryption: TLS in transit; KMS-managed encryption at rest (RDS/S3).
Secrets: AWS Secrets Manager; rotation every 90 days.
Access: SSO required; RBAC for Admin/Manager/Learner; SCIM handles lifecycle.
Retention: raw events 90 days; aggregated metrics retained for trend lines.
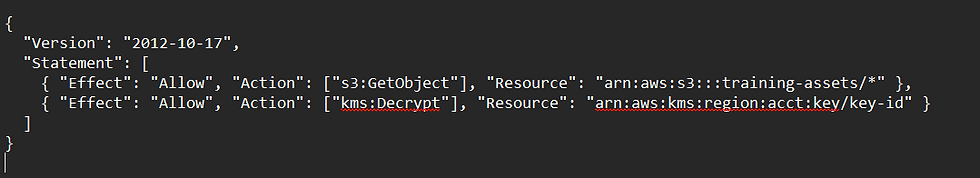
Simple IAM pattern (illustrative):
5) Curriculum & Learning Science
Tracks
Core users: password managers, MFA, device hygiene, safe links, reporting.
Execs/Finance: whaling, vendor bank changes, deepfake voice, travel OPSEC.
Developers (optional): secrets in code, SAST/DAST basics, supply chain.
Format
Micro-lessons (5–7 min), scenario-driven, one decision per lesson.
Knowledge checks (2–3 items) + “do-this-now” action (e.g., enable FIDO2 key).
Accessibility: captions, keyboard navigation, high-contrast themes (WCAG AA).
Standards mapping (so auditors smile): NIST CSF PR.AT, CIS Control 14, ISO 27001 A.7.2.2.
6) Phishing & Whaling Simulations
Phishing spectrum: domain lookalikes, QR phishing, O365 consent grants, SMS lures.
Executive drills (quarterly):
Scenario: “Urgent vendor bank change” email + deepfake voicemail from “CFO.”
Goal: force out-of-band verification (secondary channel with a shared secret).
Policy artifact: the drill ends only when the executive follows the checklist and signs an attestation; finance updates their SOP.
Example 2-step out-of-band rule we adopted:
Acknowledge the request in email/Slack.
Confirm voice-to-voice using a pre-recorded safe number and shared phrase (updated quarterly). No exceptions for “urgency.”
7) App Features That Changed Behavior
One-click “Report Phish” add-in (O365/Gmail) that forwards headers to a triage inbox and closes the loop with the reporter.
Risk score per person/team (fail rate, reporting speed, completion).
Just-in-time nudges: SMS/Slack reminders for overdue modules; automatic micro-lesson enrollments after a simulation fail.
Micro-rewards: badges, team leaderboards tied to real outcomes (first reporter of a real phish = “Firewall” badge).
8) Rollout Plan (What HR & Managers See)
Week 0–1: Connect IdP (SAML/OIDC), enable SCIM, sync HRIS groups.Week 2: Announce program + 4-week calendar; managers get talking points.Week 3–6: Core track goes live, simulations start, weekly cohort reports to managers.Week 7: Exec whaling tabletop + drill; finance S OP update.Week 8: Retrospective; publish metrics; lock in the new baseline.
Support: runbooks, a 24-hour SLA on reported phish, and a monthly “security office hour.”
9) Privacy & Compliance
DPA/SCCs in place for any vendor data flows; region-pinned S3 buckets.
Deletion by default for raw sim content; only keep outcome counters.
Audit trail for admin actions; tamper-evident logs (hash chaining in OpenSearch).
Annual penetration test on the app; continuous dependency scanning (Snyk).
10) Analytics & KPIs
Core dashboard tiles:
Completion % by org → team → individual
Phish CTR trend and distribution (95th percentile)
Time-to-report (median & P90)
Exec drill pass rate + policy adoption
Cost/learner and “hours saved” (less rework, fewer incidents)
Example CTR query (illustrative SQL):

11) Unit Economics (1,000 Learners Example)
Cost Component | Monthly |
Compute (Lambda/Fargate/API) | $70 |
Storage/CDN (S3/CloudFront) | $35 |
Auth/SSO (Auth0 tier) | $25 |
Email/SMS (SES/SendGrid/Twilio) | $25 |
Monitoring/Logs | $15 |
Estimated Total | $170 |
Pricing: $15–$29 per seat/year (+$3–$5 per exec drill).Gross margin: 85–93% at 1k seats.CAC payback: < 2 months via webinars + LinkedIn + MSP partners.
12) Outcomes (Pilot Snapshot)
92% course completion within 45 days.
Phish CTR 22% → 6% in 90 days.
TTR 11h → 47m (median).
Two real BEC attempts caught by new out-of-band policy created after exec drill.
Employee survey: 4.6/5 “usefulness,” 4.5/5 “kept it short and relevant.”
13) Risks & Mitigations
Engagement fatigue → micro-content, cap at 20 minutes/week.
Gaming simulations → rotate templates, throttle frequency per cohort.
Data sensitivity → PII minimization + strict retention.
Exec availability → 20-minute tabletops embedded in QBRs.
14) What I’d Bring to Your Team
Builder-operator: I own the full stack—requirements → architecture → content → analytics → ops.
Security + product: I talk API tokens with engineers and risk with the CFO.
ROI discipline: I design with unit economics in mind and prove impact with metrics.
Appendix: Select Artifacts
A) Terraform (illustrative) – S3 + CloudFront for training assets

B) Out-of-Band Payment Verification (one-page SOP)
All bank changes require two-channel verification (email + voice).
Use the safe-number directory; never call a number in the request.
Confirm shared phrase of the month before proceeding.
CFO/Controller co-signs change in the ERP; change log is immutable.
C) Executive Drill Script (excerpt)
Email subject: “Updated W-9 & New Banking Details”
Attachment: benign PDF; link to simulated portal (training domain).
Deepfake voicemail: “Please process today; vendor escalation risk.”
Success = exec calls safe number, rejects request, reports via add-in.
D) Nudge Email (micro-lesson reminder)
Subject: 3-minute lesson: Stop fake invoice scams Body: One short video + one question. Due Friday. Your team’s leaderboard awaits. Report your next suspicious email with the add-in—first reporter wins the “Firewall” badge.
Closing
Security programs don’t have to be expensive or boring to be effective. With the right product thinking, tight engineering, and behavior design, you can measurably lower risk while keeping the P&L healthy. If this approach aligns with your priorities, I’m happy to walk through the architecture, dashboards, and playbooks in more detail—or adapt it to your environment and scale.

Comments